Detect
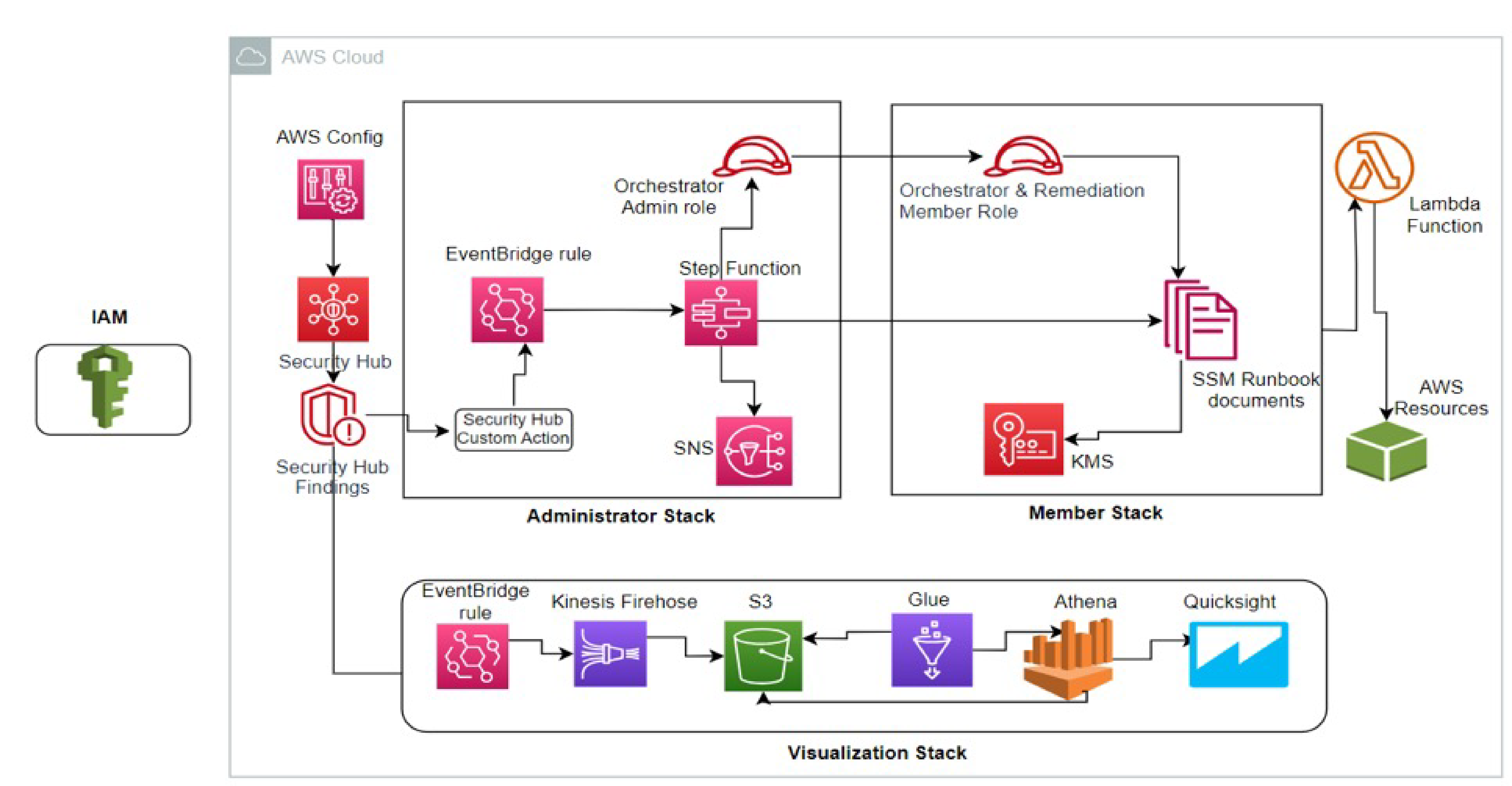
Security Hub provides you with a comprehensive view of their AWS security state. It helps you to measure your environment against security industry standards and best practices. It works by collecting events and data from other AWS services, such as AWS Config, Amazon GuardDuty, and AWS Firewall Manager.